4 ways to stop scammers and identity thieves
A few simple precautions can make all the difference.
- Just like buckling your seatbelt whenever you drive, it makes sense to take some regular precautions in navigating the digital world.
- It's important to stay vigilant even if you feel confident in your ability to spot a scam, as phishing attempts become increasingly sophisticated and difficult to identify.
- Your phone service and email have become master keys to accessing your digital information. So take steps to protect and monitor them.
- Security measures continuously evolve. Stay up to date with the latest levels of protection available on your accounts and devices.
Recent reports suggest a worrisome uptick in scams targeting customers of financial institutions. The latest versions start with a communication that seems to come from your own bank or credit union.
The scammers will make up a story, often starting with communicating over text message.
These text messages are branded to appear real and designed to engage with you, such as asking, "Do you recognize this transaction?" or "Can you confirm this payment?" They try to entice you to respond with a "yes" or a "no," or by asking you to click on a link. This can give the scammers a hook to engage you with a fraud in which they impersonate a representative of your financial institution. Then, they will try to trick you into providing your password, security code, account details, or other personal information.
The hypothetical text message below shows an example of how these fraudulent communications can begin. Note the warning signs that indicate the message is suspicious.
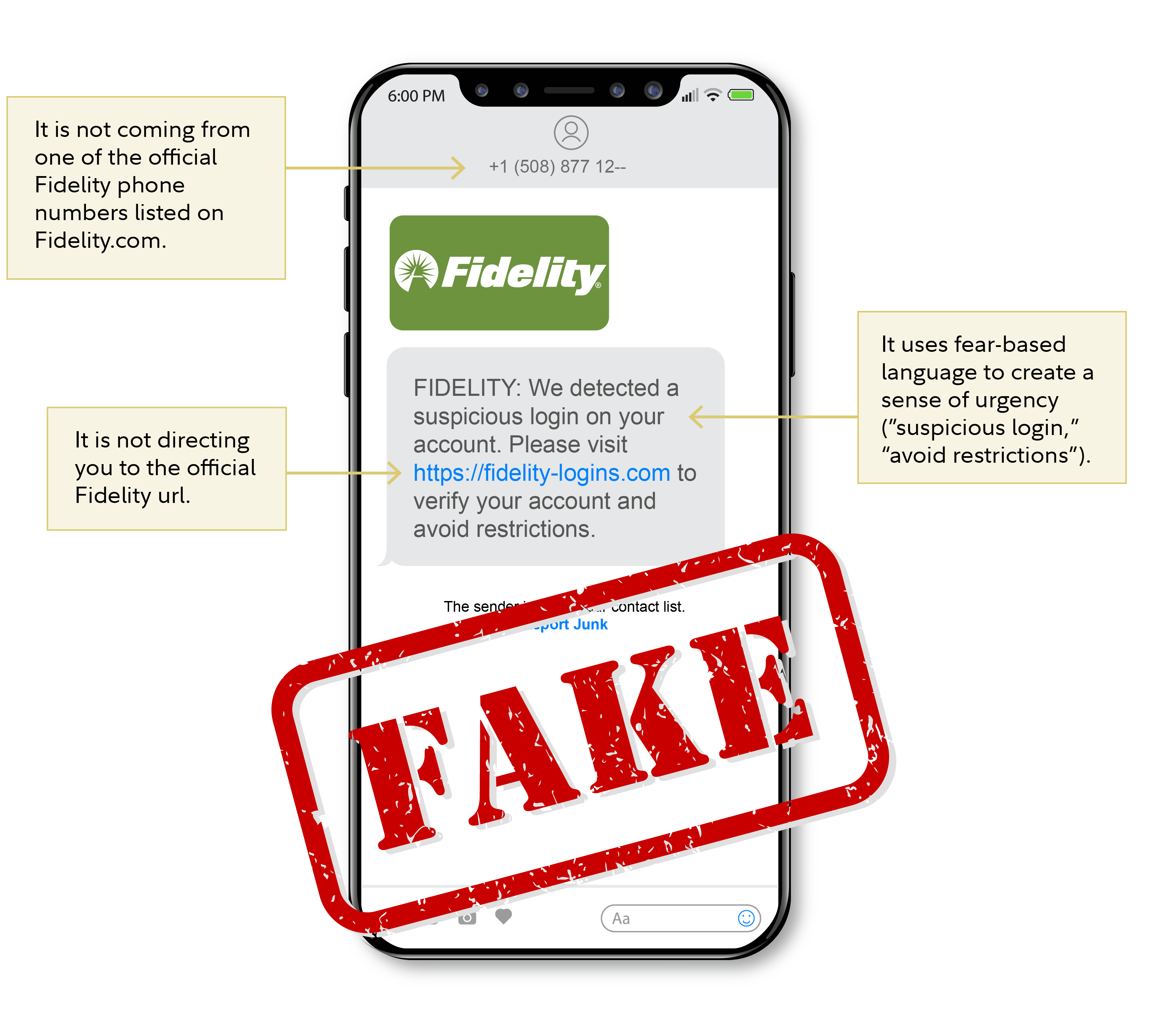
For illustration only.
The following clues may help alert you that you've received a scam communication:
- It is unexpected.
- It tries to get you to take action, potentially using language intended to create fear.
- Jumbled, misspelled, or unusual links or words.
- The sender's phone number does not match the company's published list of numbers.
- Links that are slightly different from a company's official link.
To help safeguard your identity and accounts, if you get an unsolicited text message or phone call:
- Do not click on the link, reply to the text, or answer the call.
- Never read back a security passcode (unless you have initiated the service call to a company's official phone number).
- Do not provide or "confirm" any of your personally identifying information.
- Don't trust caller ID alone if you receive an unexpected phone call. With phone calls, fraudsters can spoof legitimate phone numbers to appear trustworthy.
- Look out for suspicious texts sent as a group text. Fraudsters can set the name of a group text, so that it appears to come from a trustworthy phone number, text short code, or company name.
If you believe the message may be legitimate, contact the company through an official channel, such as a phone number listed on its website. Do not rely on a phone number provided by search-engine results.
Here are 4 more steps to protect against scams and identity theft.
1. Stay vigilant against phishing
Phishing is a technique criminals may use to try to trick you into giving them your personal information—information that they may then use to try to steal your identity, money, or other assets. They often do this by impersonating a company, institution, or government agency, and then asking you to click on a link, open an attachment, or to "confirm" your date of birth, Social Security number, or account credentials.
Even if you feel confident in your ability to spot a scam, it's important to stay vigilant in your daily life, especially as phishing attempts have become more convincing with the use of artificial intelligence (AI). Most phishing attempts are carried out by email, text message, or phone. Here are several warning signs that should raise suspicion:
Warning signs of phishing attempts
- A request for personal information or a security passcode.
- Unexpected communication claiming to be from a company you have a relationship with.
- An unfamiliar email address or phone number.
- Language that plays on your emotions or tries to get you to "act now." For example, stating that there is an issue with your financial account, offering a deal that sounds too good to be true, or claiming to be from someone who needs help.
Remember that phishers may use urgent-sounding language to try to get you to click on a link or attachment right away—before you have time to think it through. To create this sense of urgency, they might claim that something very good has happened (like you've won some money), or that something very bad has happened (like a fraudulent transaction in your financial account). Be suspicious every time you receive an unexpected text, call, or email that makes such claims. And be aware that convincing-looking images or text in a communication are commonly generated with AI, to give a fraudulent communication an appearance of legitimacy.
Here's how you can protect yourself if you've received a suspicious or unexpected communication:
Protecting yourself against phishing attempts
- Stop communication with the phisher immediately.
- Hang up the phone or ignore the suspicious email or text.
- Never read back a security passcode (unless you placed the call to a company's official phone number).
- Do not click on any links or download any attachments.
- Do not provide or "confirm" any of your personally identifying information.
- If you think the communication could be a legitimate request from a company you do business with, hang up and then call the company directly using a phone number on its official website.
- Never grant remote access to your computer unless you requested support from a trusted source.
2. Strengthen your account security
Many companies go to great lengths to safeguard customers' information and accounts, and are continually working to build new and enhanced layers of protection.
You can help reinforce those safeguards by being cautious with your passwords, opting in for new security measures, and making sure the companies you work with know how to reach you if they ever need to.
Here are some proactive steps you can take to strengthen your account security:
Protecting your financial and other accounts
- Set up online access for your accounts. Use a unique, long password or passphrase for each account and change it if you believe it's been compromised.
- Make sure your institutions have up-to-date phone and email contact information for you.
- Sign up for multi-factor authentication, when available.
- Consider enrolling in eDelivery to help reduce the risk of theft of paper documents that can contain sensitive information.
- Sign up for automated alerts of suspicious account activity, when available.
- Regularly monitor your accounts, including login history, profile and beneficiary information, and transactions.
3. Protect your phone service and email address
If criminals can gain access to your phone calls, text messages, voicemails, or emails, they can potentially steal personal information or one-time passcodes—enabling them to break into your accounts.
Here are several warning signs not to ignore:
Warning signs that your phone or email has been compromised
- You stop receiving phone calls, text messages, or email notifications.
- Your phone says "no service" or "emergency calls only."
- Your cell or email provider notifies you of changes to your account.
- Messages are being sent from your email or cell number that you did not originate.
If you notice any of these warning signs, contact your provider right away to see if your account has been compromised. You can also take some proactive steps to help better protect your accounts:
Protecting your cell phone and email against hackers
- Set up online access for your mobile account, if you haven't already.
- Take advantage of the security features your providers offer, such as multi-factor authentication or security alerts.
- Use a unique password and, when available, set up a PIN. Reset them if you believe they've been compromised.
4. Secure your devices
Finally, any device you use that's connected to the internet can become an avenue for cybercriminals to attack. Hackers may get in through newly discovered security weaknesses in these devices and systems. From there, they may also be able to record your keystrokes, access your personal information, or even break into your accounts.
Here are some measures you can take to help secure your devices:
Protecting your devices from cybercriminals and fraudsters
- Apply operating system and application patches as soon as they are released.
- Avoid conducting financial or other sensitive transactions, including money movement, online shopping, or checking email or social-media accounts, using shared devices or unsecure networks.
- Change all default passwords that come with your devices, including smart home technology.
- Only download apps from an approved vendor app store.
- Run antivirus and personal firewall software.
- Avoid public Wi-Fi unless you are taking steps to encrypt and protect your activity, such as by using a personal virtual private network (VPN).
In conclusion
Protecting your information and accounts can help avoid the hassle and heartache of identity theft and fraud.
In addition to the proactive measures mentioned above, a few more steps may help you defend against, detect, or respond promptly to suspicious activity. Monitoring your credit reports regularly for any suspicious activity—such as profile changes, transaction attempts, or unfamiliar activity—can help you detect suspicious events quickly. Freezing your credit can be a powerful line of defense as it prevents lenders from accessing your credit report, to stop fraudsters from borrowing money in your name.
If you believe you have been a victim of identity theft, a scam, or a cybercrime, there are government resources that may help you.
- To report identify theft and establish a recovery plan, visit the Federal Trade Commission's Identity Theft page.
- To report a scam, visit the Federal Trade Commission.
- To report a cybercrime, visit the FBI's Internet Crime Complaint Center.
Related insights
View all


Fidelity does not provide legal or tax advice. The information herein is general and educational in nature and should not be considered legal or tax advice. Tax laws and regulations are complex and subject to change, which can materially impact investment results. Fidelity cannot guarantee that the information herein is accurate, complete, or timely. Fidelity makes no warranties with regard to such information or results obtained by its use, and disclaims any liability arising out of your use of, or any tax position taken in reliance on, such information. Consult an attorney or tax professional regarding your specific situation.
The third-party trademarks and service marks appearing herein are the property of their respective owners.
Fidelity Investments® provides investment products through Fidelity Distributors Company LLC; clearing, custody, or other brokerage services through National Financial Services LLC or Fidelity Brokerage Services LLC; and institutional advisory services through Fidelity Institutional Wealth Adviser LLC.





